The Analysis sheet lets you easily identify areas for improvement
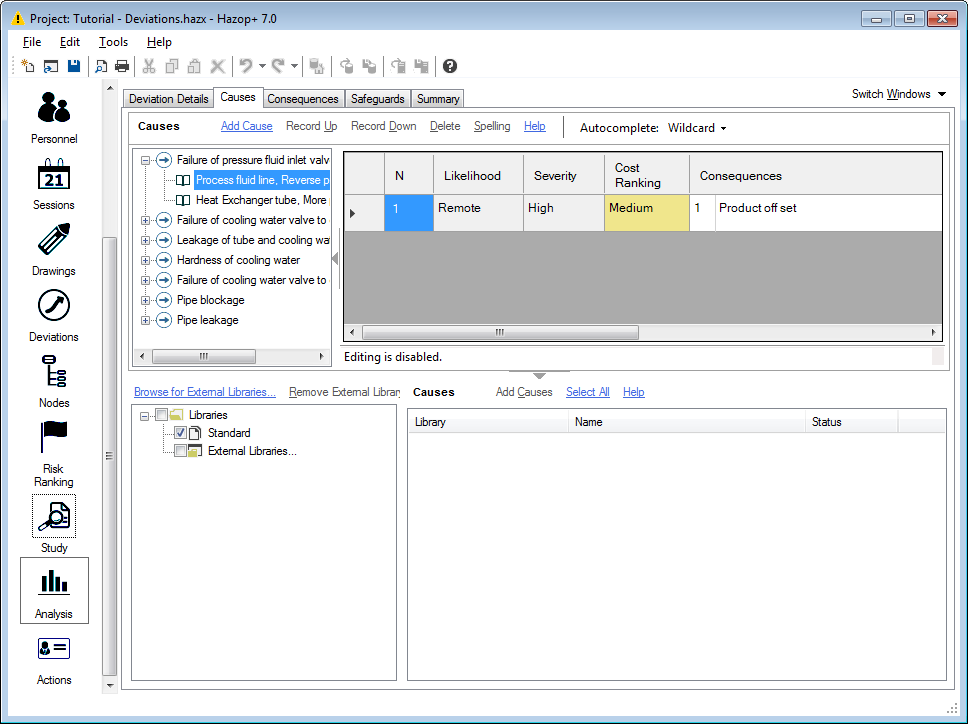
Causes
The Causes tab allows the user to enter and view information relating to the causes associated with the Hazop Study.
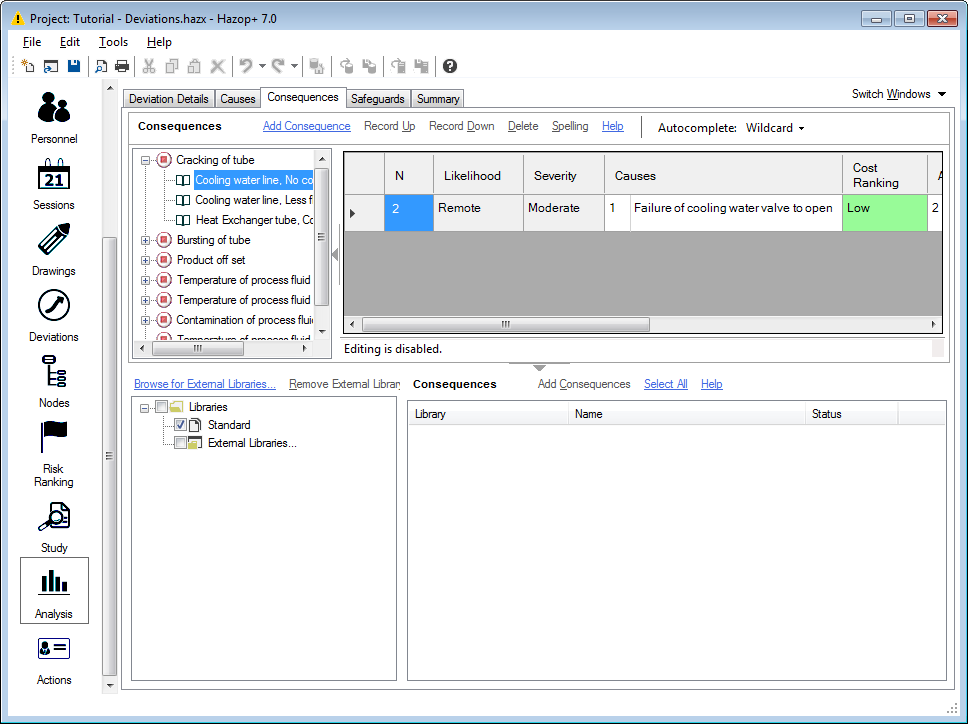
Consequences
The Consequences tab gives easy access to the consequence data within Hazop+.
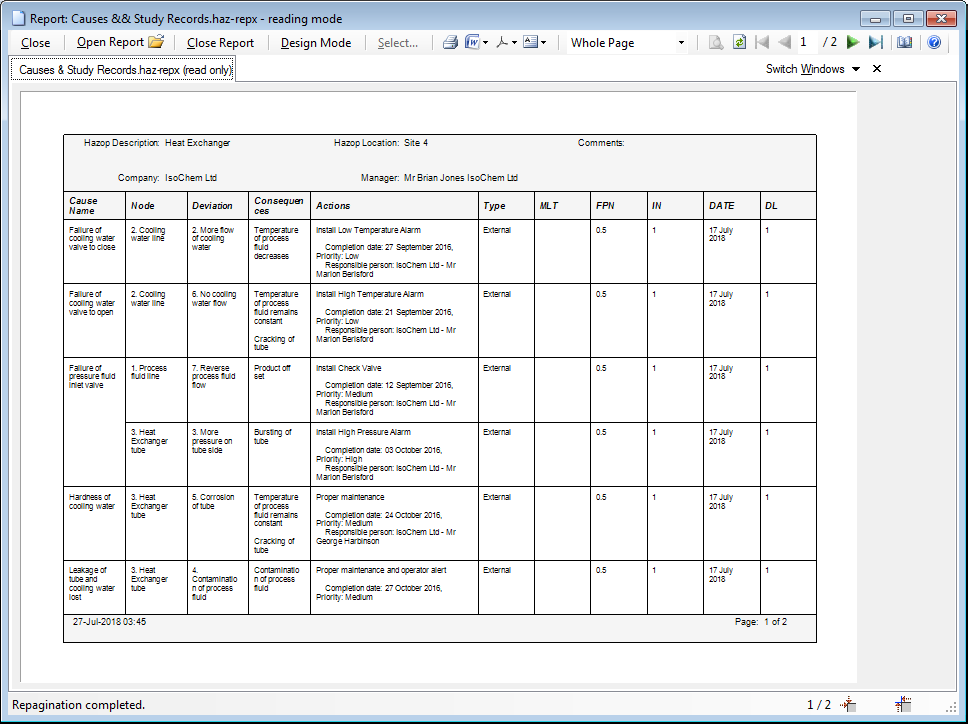
Safeguards
The Safeguards tab lets you quickly view all the safeguards put in place in your study.
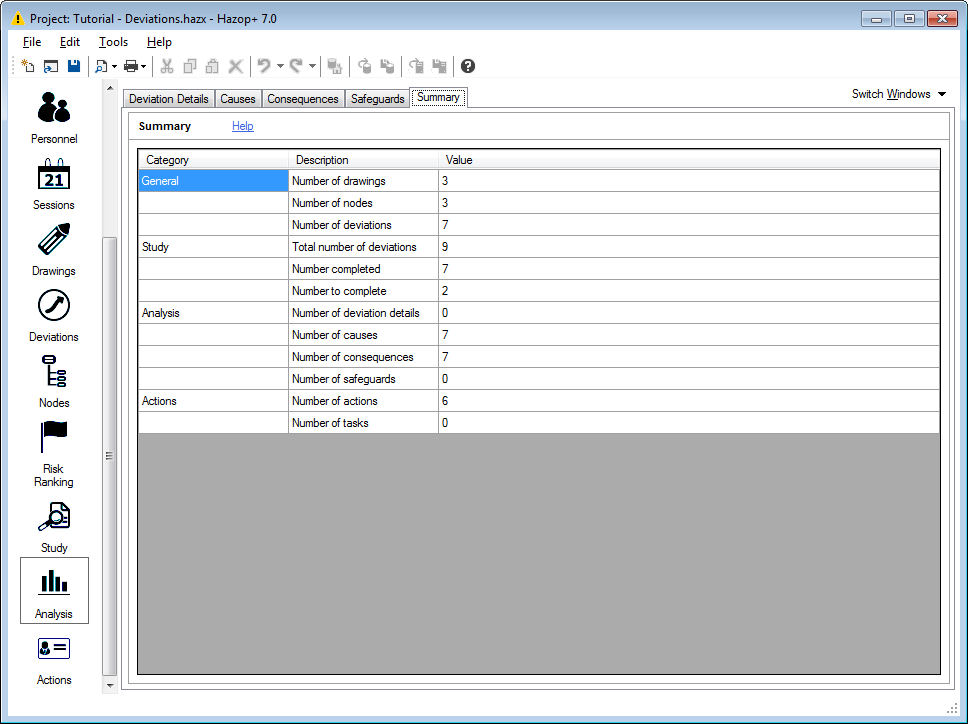
Summary
The Summary tab provides a table with details of how many different types of information appear in the Hazop+ database. For example, amongst many other statistics, you can see the total number of deviations within the study.