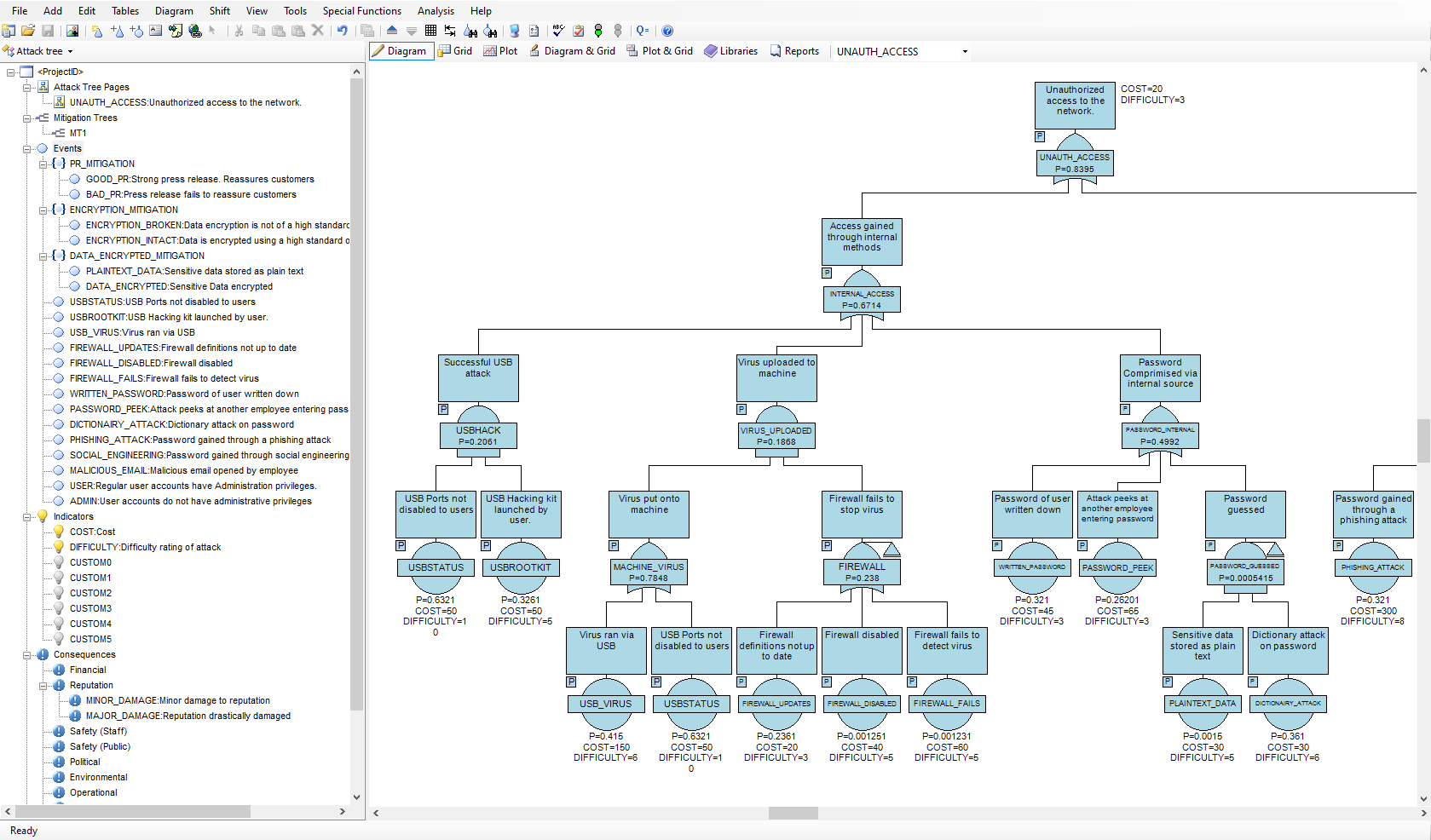
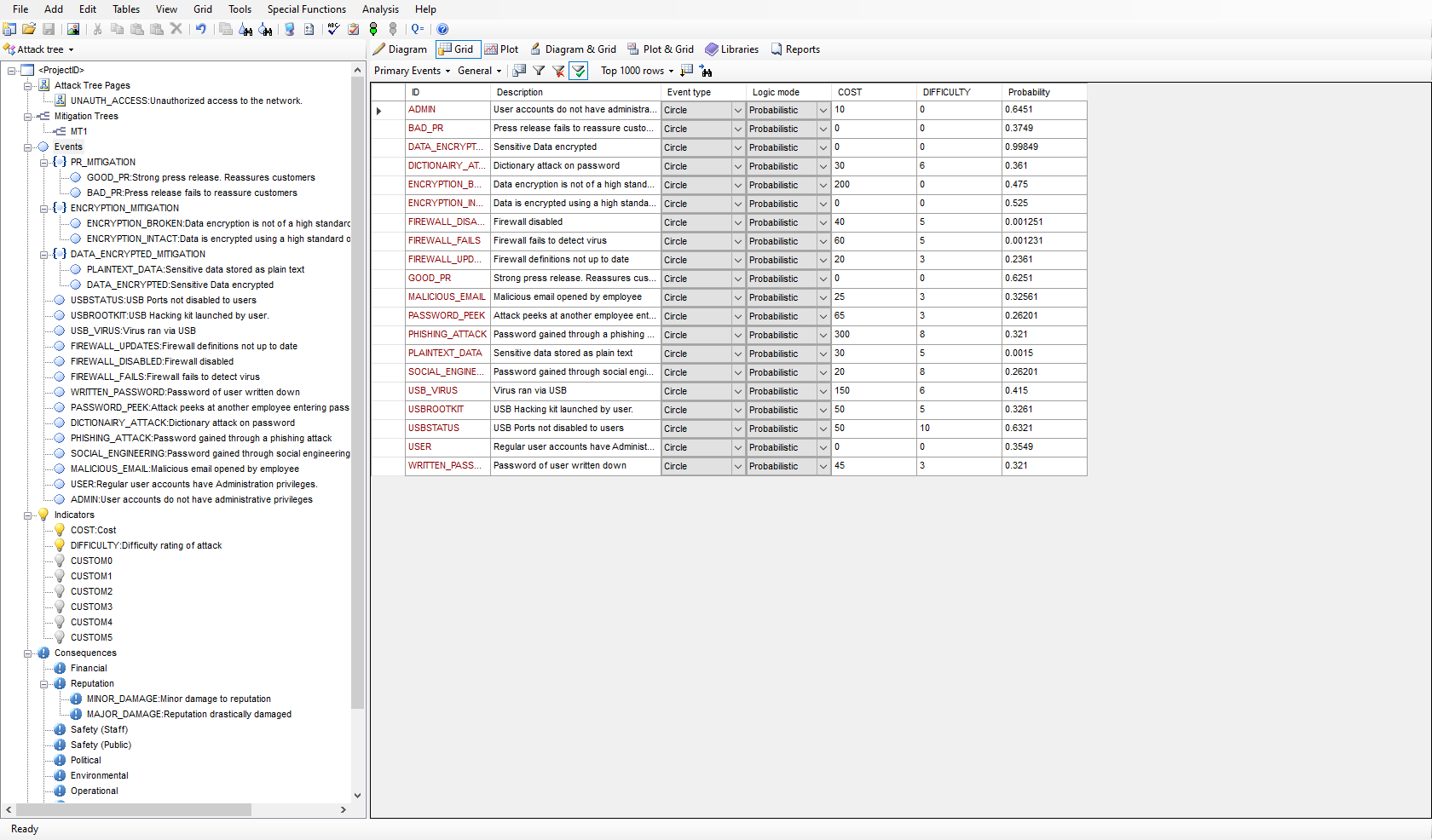
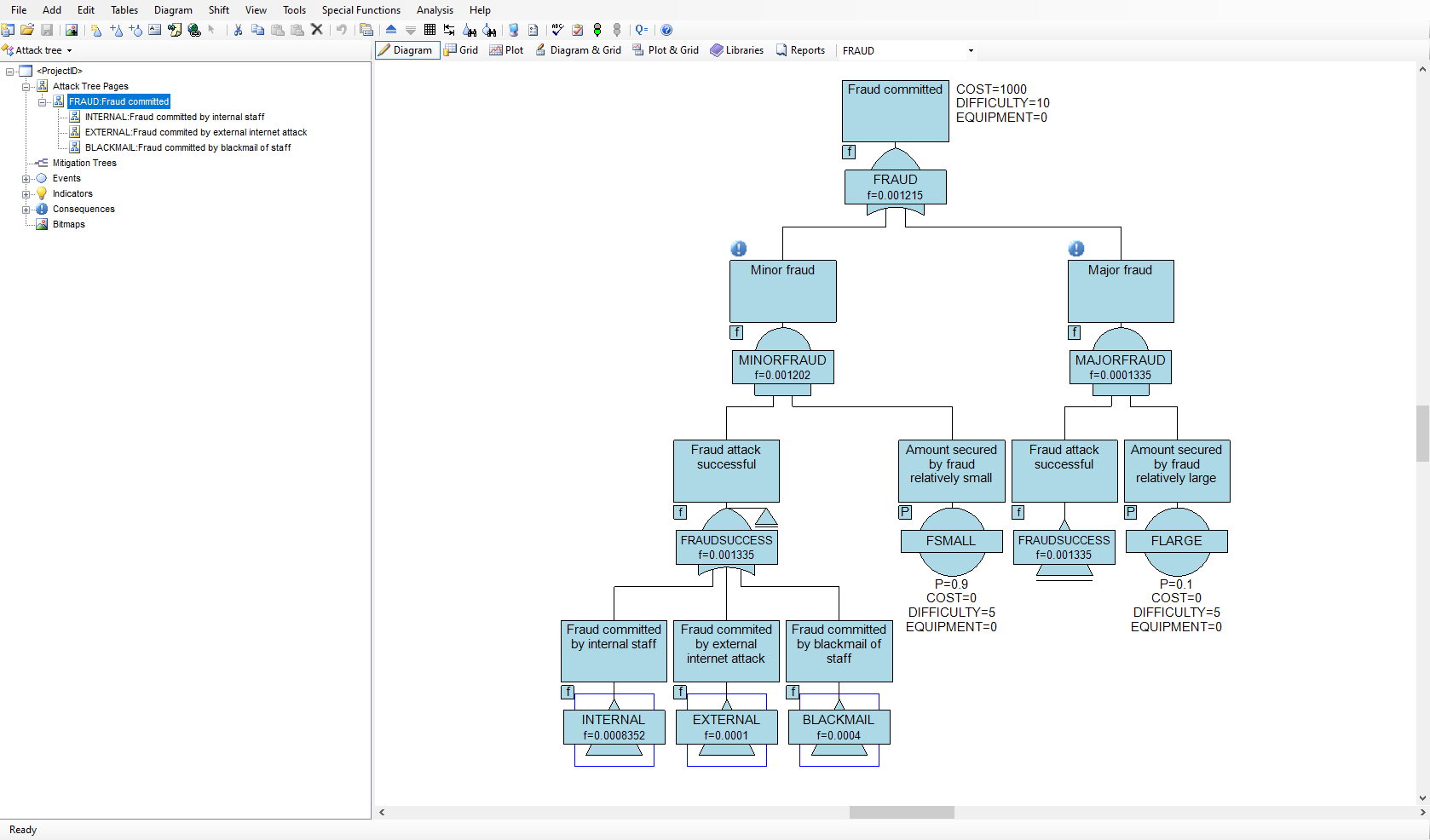
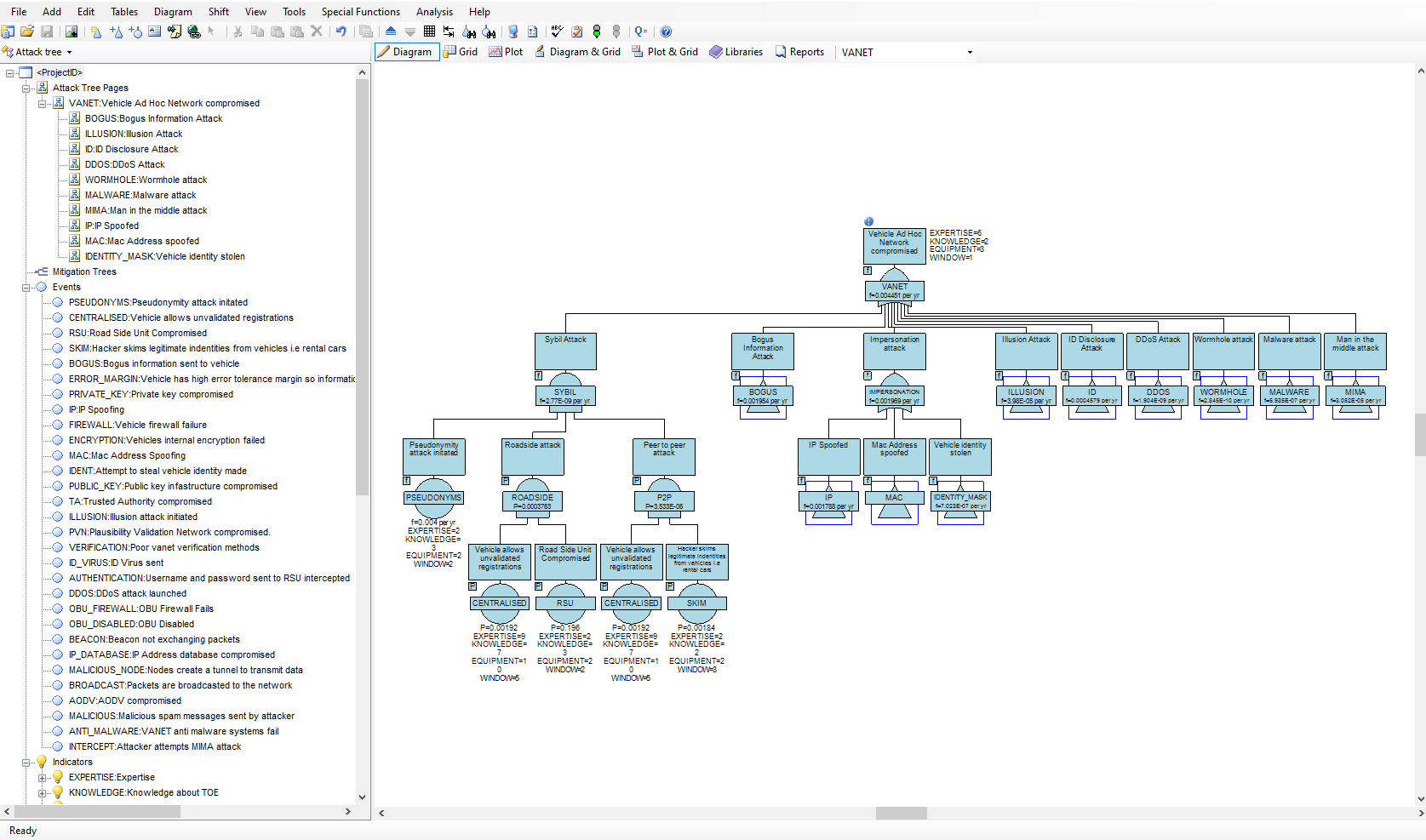
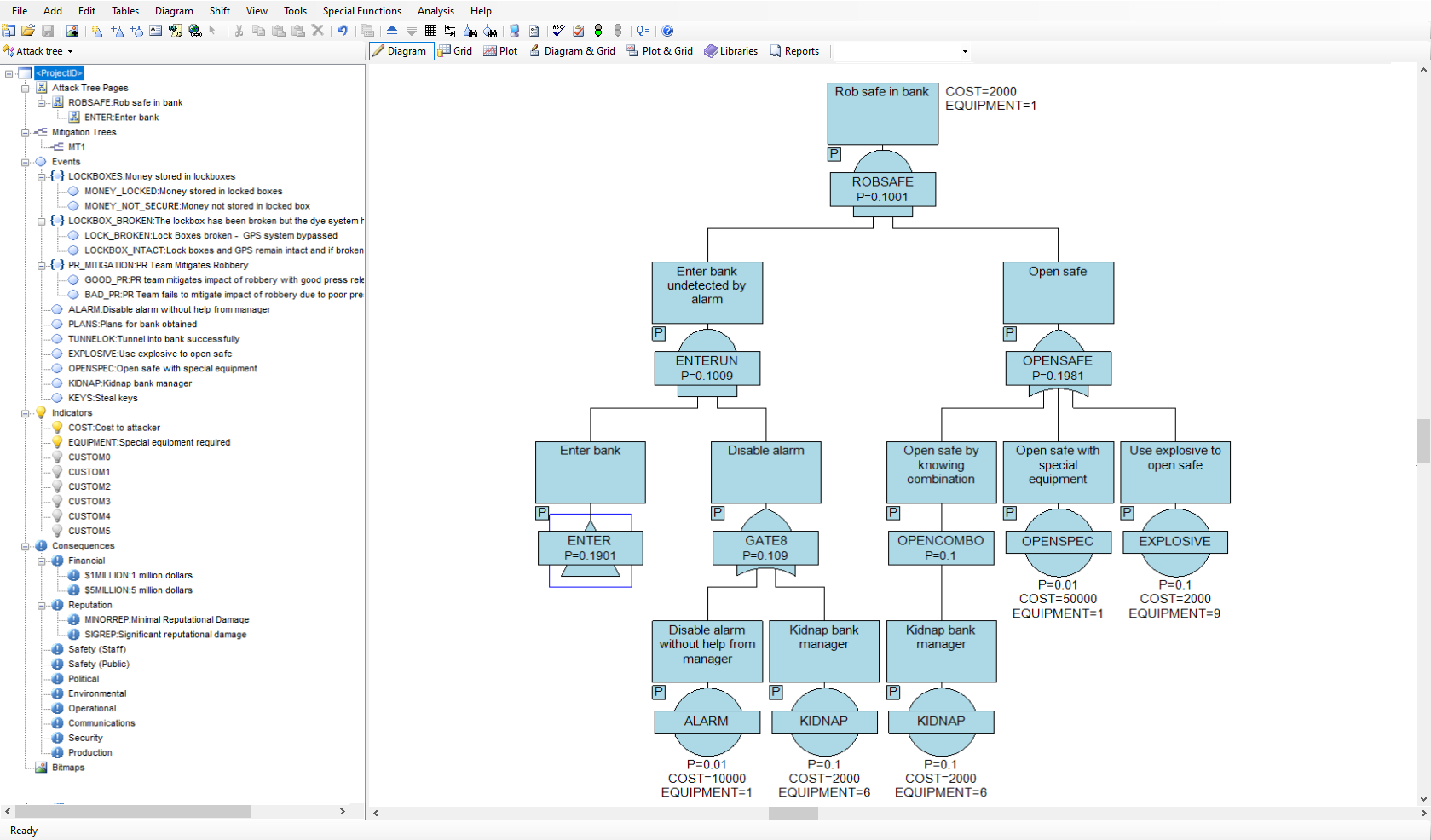
Attack trees allow threats against system security to be modeled concisely in an easy to understand graphical format. The effectiveness of cybersecurity, network security, banking system security, installation and personnel security may all be modeled using attack trees. With the increased risk of terrorist attacks on homeland security, hacking attacks on computer systems and computer-based fraud on banking systems, attack tree analysis is an invaluable tool for system designers and security personnel.
Visualize Potential Attack Scenarios
Attack tree analysis provides a method to model the threats against a system in a graphical easy-to-understand manner. If we understand the ways in which a system can be attacked we can develop countermeasures to prevent those attacks achieving their goal.
The Methodology
In order for an attack to succeed, the attack has to be initiated, and various barriers overcome by the attacker. There may be different ways in which an individual or team could mount an attack on a system and there may be different levels of defence against different types of attack. Attack trees provide a graphical representation on how attacks might succeed and allow a probabilistic analysis on which attacks are most likely to succeed. The methodology can also reveal the vulnerability of your system under specified constraints. For example, what are the most probable ways in which an attack will succeed in its objective at a relatively low cost to the attacker.
Using AttackTree
The AttackTree software provides a sophisticated environment in which to quickly build and analyze attack tree models and present the results in an easy to understand format. AttackTree also allows users to define indicators that quantify the cost of an attack, the operational difficulty in mounting the attack, and any other relevant quantifiable measure that may be of interest. Questions such as ‘which attacks have the highest probability of success at a low cost to the attacker?’ or ‘which attacks have the highest probability of success with no special equipment required?’ can be answered using AttackTree. In AttackTree, different categories and levels of consequence may also be assigned to nodes in the attack tree. A successful attack may have financial, political, operational and safety consequences. A partially successful attack may have a different level of consequence to a totally successful attack. All these types of consequence measure may be modelled in AttackTree.